In our increasingly connected world, where every digital interaction seems to leave a trace, a common question often arises about the privacy of our communications: can people see when I listen to their voicemail? This seemingly simple query delves into the intricate workings of telecommunication systems, data collection practices, and the subtle nuances of digital privacy that most of us rarely consider. Understanding whether your voicemail listening activity is visible to others is not just about curiosity; it's about comprehending the extent of data transparency in our daily lives and managing our digital footprint effectively. From the moment a call is made to the second a voicemail is retrieved, a complex network of servers, carriers, and protocols is at play, each potentially logging information. This article aims to demystify the process, offering a comprehensive look at what happens behind the scenes when you access a voicemail, what data is typically collected, and whether the person who left the message has any visibility into your listening habits.
The digital age has brought unprecedented convenience, but it has also introduced new layers of complexity regarding personal data and privacy. Voicemail, a technology that has been around for decades, has evolved alongside our smartphones and integrated communication platforms. While it might seem like a straightforward audio message, the underlying infrastructure and data handling practices are far from simple. Many individuals are concerned about whether their interactions with such systems are truly private, or if there's a digital trail that reveals when and how they engage with messages. Let's explore the technical realities and common practices to provide a clear answer to this pressing privacy question.
Table of Contents
- The Digital Echo Chamber: Understanding Voicemail Systems
- The Core Question: Can People See When I Listen to Their Voicemail?
- Technical Realities: What Data Do Voicemail Systems Collect?
- Carrier Policies and Privacy Statements
- Beyond Voicemail: Your Broader Digital Footprint and Privacy
- Protecting Your Privacy: Best Practices for Digital Communications
- Dispelling Myths and Setting Expectations
- The Evolving Landscape of Digital Privacy
The Digital Echo Chamber: Understanding Voicemail Systems
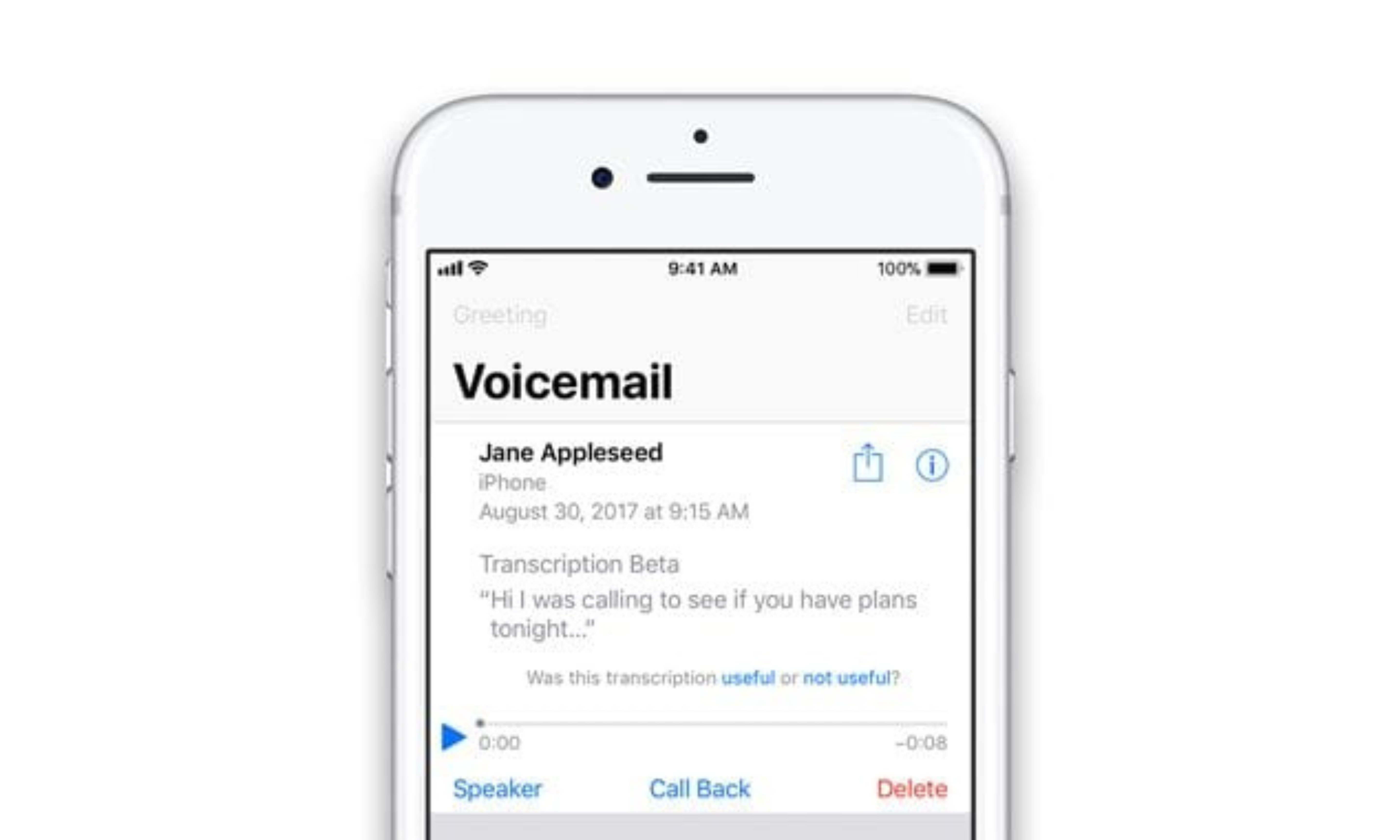
Voicemail, at its core, is a sophisticated answering machine service provided by telecommunication carriers. When a call goes unanswered, the network routes the caller to a dedicated voicemail server. This server records the message and stores it, typically as an audio file, associated with the recipient's phone number. The recipient is then notified of a new message, usually via an SMS or a visual voicemail notification on their smartphone. The process of retrieving a voicemail involves the recipient connecting to this server, authenticating themselves, and then playing the stored audio file. This entire interaction, from message recording to retrieval, is managed by the carrier's infrastructure.How Voicemail Technology Functions
Modern voicemail systems are integral components of a carrier's network infrastructure. When a caller leaves a message, it's not simply stored on your phone; it resides on a secure server maintained by your mobile carrier or a third-party provider they partner with. When you check your voicemail, your phone communicates with this server. This communication involves authentication (like entering a PIN) and then a request to stream or download the audio file. For visual voicemail, the audio is often transcribed into text by the server before being sent to your phone, allowing you to read messages without listening to them. Each step in this digital chain, from the initial call routing to the final message retrieval, generates data logs. These logs are crucial for the carrier's operational purposes, such as billing, troubleshooting, and network management. They track call durations, timestamps, and successful connections, but the level of detail regarding specific user actions like "listening to a voicemail" is where privacy questions arise.The Illusion of Anonymity in Digital Communications
In the digital realm, true anonymity is often an illusion. Every online interaction, every call, every message sent or received, leaves a digital footprint. While we might feel our individual actions are private, the underlying systems are designed to log and process vast amounts of data. This data is essential for the functionality and maintenance of these services. For instance, a carrier needs to know if a voicemail message was successfully delivered and accessed to ensure their service is working correctly. This necessity for operational data often blurs the lines with personal privacy. The question of "can people see when I listen to their voicemail" taps into this broader concern about how much of our digital lives are truly private versus how much is recorded and potentially accessible by others, even if only in aggregated or anonymized forms. It highlights the importance of understanding not just what data is collected, but also who has access to it and for what purposes.The Core Question: Can People See When I Listen to Their Voicemail?
Let's get straight to the heart of the matter: **No, in the vast majority of standard voicemail scenarios, the person who left you a message cannot directly see or receive a notification that you have listened to their voicemail.** This is a fundamental aspect of how voicemail systems are designed for privacy. Unlike messaging apps that might show "read receipts" or "seen" statuses, traditional voicemail systems do not provide this functionality to the caller. When you access your voicemail, whether by dialing into the service or using a visual voicemail interface, you are interacting with your own voicemail inbox hosted by your carrier. Your activity within that inbox – such as playing, saving, or deleting messages – is generally private to you and your carrier. The system's primary function is to deliver the message to you and manage your inbox, not to provide detailed listening analytics back to the message sender. However, it's crucial to understand the nuances. While the caller won't get a "listened" notification, the carrier *does* log that the message was accessed. This information is for internal operational purposes, not for sharing with the caller. For instance, if a message is marked as "new" until you listen to it, the system needs to record that you've listened to it to change its status. But this internal logging is distinct from providing a direct notification to the original sender. The only exceptions to this general rule would be highly specialized, non-standard communication platforms or business-grade phone systems that might be configured to provide such detailed tracking for internal purposes (e.g., a customer service department tracking if a manager listened to a specific customer's message). For personal mobile phone voicemails, however, you can rest assured that the sender is not notified when you listen to their message. The privacy concern around "can people see when I listen to their voicemail" is largely unfounded for typical consumer services.Technical Realities: What Data Do Voicemail Systems Collect?
While the sender cannot see when you listen to their voicemail, it's important to understand that telecommunication carriers do collect a significant amount of data related to call and voicemail activity. This data is not typically shared with individual users in a way that compromises your privacy regarding specific listening events, but it forms a comprehensive record of network usage.Call Detail Records (CDRs) and Their Implications
Call Detail Records (CDRs) are the backbone of telecommunications data. These records are generated for every call and interaction on a carrier's network. For a voicemail, a CDR would typically include:- The caller's phone number.
- The recipient's phone number.
- Date and time the voicemail was left.
- Duration of the voicemail message.
- Date and time the voicemail was accessed/retrieved by the recipient.
- Duration of the access session.
- The type of interaction (e.g., message left, message retrieved).
Server Logs and Access Information
Beyond CDRs, voicemail servers maintain detailed logs of all interactions. These server logs are even more granular, recording every command and action performed on the system. When you log in to your voicemail box, the server records your authentication, the messages you access, whether you play them, save them, delete them, or forward them. These logs are essential for the system's functionality, security, and auditing. For example, if there's a technical issue with message delivery or retrieval, these logs provide a trail for engineers to diagnose the problem. The key takeaway here is that while the data exists, it is stored securely by the carrier and is subject to their privacy policies and legal regulations. It is not designed to be shared with the person who left the message. The information collected is for the carrier's operational and business needs, not for revealing your voicemail listening habits to others. The concern "can people see when I listen to their voicemail" is therefore addressed by understanding that while data is logged, it's not made visible to the sender.Carrier Policies and Privacy Statements
Every major telecommunications carrier operates under strict privacy policies and is subject to various regulations regarding customer data. These policies typically outline what data is collected, how it is used, and under what circumstances it might be shared. When you sign up for mobile service, you implicitly agree to these terms. A review of common carrier privacy statements (e.g., Verizon, AT&T, T-Mobile in the US, or major providers globally) consistently shows that while they collect data on call records, messaging, and data usage, they do not list "voicemail listening status shared with sender" as a feature or a data point shared with third parties, including the person who left the message. Their primary obligation is to protect the privacy of their subscribers' communications. Sharing such specific interaction data would be a significant breach of that trust and would likely violate privacy regulations. For example, carriers are legally obligated to provide customer data only under specific circumstances, such as a valid court order, subpoena, or warrant. Even in such cases, the data provided would be the internal logs and CDRs discussed earlier, not a notification system for the message sender. Therefore, the answer to "can people see when I listen to their voicemail" remains firmly no, based on standard carrier practices and privacy commitments. These policies are designed to build trust and ensure that users feel secure in their communications.Beyond Voicemail: Your Broader Digital Footprint and Privacy
While the specific concern about whether **can people see when I listen to their voicemail** is largely unfounded, it serves as an excellent entry point into a much larger and more critical discussion: the entirety of your digital footprint and the pervasive nature of data collection in the modern world. Every interaction we have with digital tools, from sending an email to browsing social media, contributes to a vast ocean of data. Understanding this broader landscape is key to navigating privacy in the 21st century. Consider the myriad of digital tools we use daily for communication, work, and creativity. These platforms, while incredibly convenient and powerful, are designed to collect data to function, improve, and often, to monetize. Take, for instance, creative design platforms. Many individuals and businesses rely on tools that simplify complex tasks, making professional-grade content accessible to everyone. You can **explore thousands of beautiful free templates** on such platforms, and **with Canva's drag and drop feature, you can customize your design for any occasion in just a few clicks.** This ease of use is a hallmark of modern digital tools. The accessibility of these platforms is remarkable. **Canva is always free for every individual, however, if you want to unlock premium features, individuals can upgrade to Canva Pro to easily create professional designs and content.** This freemium model encourages widespread adoption, allowing millions to **create anything in a snap, from presentations and logos to social media posts.** Users can **get inspired and see what you can do on Canva, no design skills or experience required.** The ability to **elevate your work with Canva Pro’s premium features and AI tools** means that even complex design tasks are streamlined. You can **easily create stunning social media content, photos, videos, presentations, and more.** The sheer versatility is evident: **unleash your creativity with Draw, Canva’s free drawing tool. Draw lets you add customized drawings and graphics to your designs, so they stand out from the crowd.** Or, you can use it to **promote your tours and packages with travel agency templates you can customize and share from Canva.** You can even **set the table in style with good designs from dinner templates you can personalize and share from Canva.** The platform facilitates collaboration, allowing you to **create beautiful designs with your team.** The ease of access is further highlighted by flexible login options: **login with your email address, mobile number, Google, Facebook or Apple.** This integration with various services underscores how interconnected our digital lives are. Furthermore, you can **navigate your message perfectly with world map templates you can customize to visualize travel ideas, geography lessons, global reports, creative projects, and more.** Even practical needs are met: **you can create a CV for free using our free visual design platform. We have a gallery filled with hundreds of professionally designed and free CV templates to fit a range of industries, theme,** and so on. The global reach is also notable, with the platform being described as **"Canva es una herramienta online de diseño gráfico de uso gratuito, Utilízala para crear publicaciones para redes sociales, presentaciones, carteles, vídeos, logos y mucho más,"** and **"O Canva é uma ferramenta gratuita de design gráfico online que você pode usar para criar posts para redes sociais, apresentações, cartazes, vídeos, logotipos e muito mais."** These statements in Spanish and Portuguese highlight the platform's universal appeal and accessibility across different languages and regions. Every time you interact with such a platform – whether you're uploading an image, using an AI tool, or logging in – data is generated and processed. This includes usage patterns, feature engagement, and sometimes even content analysis (depending on the platform's terms). While this data is crucial for providing and improving the service, it collectively forms a comprehensive digital profile of you. This broader context is vital: understanding how data is collected and used by creative tools like Canva, or even simple login methods, provides a clearer picture of the digital ecosystem. It reinforces the idea that while specific privacy concerns like "can people see when I listen to their voicemail" might be unfounded, a general awareness of your digital footprint across all platforms is essential for maintaining your overall privacy and security.Protecting Your Privacy: Best Practices for Digital Communications
Even though the direct answer to "can people see when I listen to their voicemail" is generally no, adopting good digital privacy habits is crucial in today's interconnected world. Here are some best practices to enhance your overall privacy in digital communications:- Use Strong, Unique Passwords: This is fundamental. For your voicemail PIN and all online accounts, use complex, unique passwords that are difficult to guess. Consider using a password manager.
- Enable Two-Factor Authentication (2FA): Wherever possible, enable 2FA for your accounts, especially those linked to your phone number or email. This adds an extra layer of security beyond just a password.
- Be Mindful of What You Share: Think twice before sharing personal information in voicemails or any digital communication. Once information is out there, it's hard to retract.
- Regularly Review Privacy Settings: Many apps and services have customizable privacy settings. Take the time to review and adjust them to your comfort level. This includes social media, messaging apps, and even your phone's system settings.
- Understand App Permissions: When installing new apps, pay attention to the permissions they request. Does a messaging app really need access to your location or microphone when not in use?
- Secure Your Devices: Use screen locks, encryption, and keep your operating system and apps updated to the latest versions. Updates often include critical security patches.
- Be Skeptical of Unsolicited Messages: Be wary of phishing attempts via email or text messages that try to trick you into revealing personal information. Never click on suspicious links.
- Consider Encrypted Communication: For highly sensitive conversations, use end-to-end encrypted messaging apps (e.g., Signal, WhatsApp) that ensure only the sender and receiver can read the messages.
- Educate Yourself: Stay informed about common privacy threats and new technologies. The more you understand, the better equipped you are to protect yourself.
Dispelling Myths and Setting Expectations
The internet is rife with misconceptions about digital privacy, and the question of "can people see when I listen to their voicemail" is a perfect example of a common concern that often stems from a lack of clear information. It's important to differentiate between what's technically possible, what's standard practice, and what's a myth. One common myth is that carriers actively monitor and share specific user interactions like voicemail listening with third parties without consent. As discussed, while data is logged for operational purposes, it is not shared with the message sender. Another misconception is that simply having a smartphone means all your activities are inherently public. While smartphones are data-rich devices, privacy controls and regulations exist to protect user information. Setting realistic expectations about digital privacy means understanding that no system is 100% private or secure. There's always a theoretical possibility of sophisticated surveillance or data breaches, but these are distinct from standard operational procedures. For everyday use, your voicemail interactions are private between you and your carrier. The expectation should be that your carrier uses your data responsibly, as outlined in their privacy policy, and that they will not disclose specific listening events to the person who left the message. This distinction is crucial for maintaining a healthy perspective on digital privacy without succumbing to unnecessary paranoia.The Evolving Landscape of Digital Privacy
The discussion around "can people see when I listen to their voicemail" is a snapshot of a much larger, constantly evolving landscape of digital privacy. As technology advances, so do the capabilities for data collection and analysis. From the rise of AI-powered services to the increasing integration of IoT devices into our homes and lives, the sheer volume of data being generated and processed is unprecedented. Regulations like GDPR in Europe and CCPA in California are attempts to provide individuals with more control over their data, but the global nature of the internet makes comprehensive oversight challenging. Companies are continually innovating, and with that comes new ways of interacting with data. For instance, the advent of voice assistants and smart speakers means that our spoken words are increasingly being processed by algorithms. Similarly, advancements in network monitoring and analytics mean that telecommunication companies have even more granular insights into network usage. This continuous evolution necessitates ongoing vigilance and education. Users must remain informed about their rights, the technologies they use, and the privacy implications of their digital choices. The question of voicemail privacy, while specific, highlights a universal truth: in the digital age, understanding how our data is handled is not just for tech experts, but for every individual navigating an increasingly data-driven world. The conversation around digital privacy is far from over; it's a dynamic dialogue that will continue to shape our interactions with technology for years to come.In conclusion, the direct answer to whether **can people see when I listen to their voicemail** is a resounding no, under normal circumstances. Standard voicemail systems are designed to protect the privacy of the recipient, ensuring that the sender does not receive notifications about when or if their message has been heard. While telecommunication carriers do log data about voicemail access for operational purposes, this information is internal and not shared with the message sender.
However, this specific query serves as a valuable gateway to a broader understanding of digital privacy. Every interaction in our digital lives, from creative design work to simple phone calls, contributes to a digital footprint. Understanding the data practices of the tools we use daily, like the versatile design platform Canva, helps us grasp the larger context of data collection and privacy in the modern world. By adopting robust digital hygiene practices, such as using strong passwords, enabling two-factor authentication, and being mindful of information sharing, individuals can significantly enhance their overall privacy and security.
Ultimately, navigating the digital landscape requires a combination of informed awareness and proactive measures. While you can rest easy knowing your voicemail listening is private from the sender, cultivating a comprehensive approach to digital privacy will serve you well in an ever-evolving technological environment. What are your thoughts on digital privacy in the age of pervasive data collection? Share your insights in the comments below, and consider exploring our other articles on safeguarding your digital identity.


Detail Author:
- Name : Fanny Koepp
- Username : kunze.keira
- Email : lkunde@yahoo.com
- Birthdate : 1996-10-02
- Address : 9319 Myrtie Passage South Preston, PA 89818
- Phone : 469-896-2257
- Company : Rutherford PLC
- Job : Welder
- Bio : Quis quisquam quibusdam autem placeat eligendi molestiae. Doloribus odio dolorem aut illum libero quod sequi.
Socials
tiktok:
- url : https://tiktok.com/@emery.walsh
- username : emery.walsh
- bio : Autem optio voluptas cupiditate.
- followers : 1509
- following : 120
facebook:
- url : https://facebook.com/walshe
- username : walshe
- bio : Vitae reprehenderit quos est perferendis ipsam commodi.
- followers : 1737
- following : 593
linkedin:
- url : https://linkedin.com/in/emery_walsh
- username : emery_walsh
- bio : Aliquam dolores eos sequi et eum ducimus.
- followers : 5388
- following : 786
twitter:
- url : https://twitter.com/emery_walsh
- username : emery_walsh
- bio : Eum vel ipsam illo eaque aliquam qui. Totam porro voluptas mollitia voluptas. Quam est suscipit quae quas et in quo. Iusto a quos dicta est.
- followers : 4627
- following : 1791